Reposted from February 2022
Congratulations on your vExpert Award!
I was very honored to receive another vExpert award this past year! This made it 10 years in a row for me!!
One of the most useful perks for achieving the vExpert is given by Pluralsight which offers a 1-year full access to its technology learning platform for vExperts and many other VIP programs.
If you are a vExpert, or other VIP, check out pluralsight.com/teach/resource/vips for details.
And congratulations to all of the 2022 vExperts!!
Congratulations on your vExpert Award!
I was very honored to receive another vExpert award this past year! This made it 10 years in a row for me!!
One of the most useful perks for achieving the vExpert is given by Pluralsight which offers a 1-year full access to its technology learning platform for vExperts and many other VIP programs.
If you are a vExpert, or other VIP, check out pluralsight.com/teach/resource/vips for details.
And congratulations to all of the 2022 vExperts!!



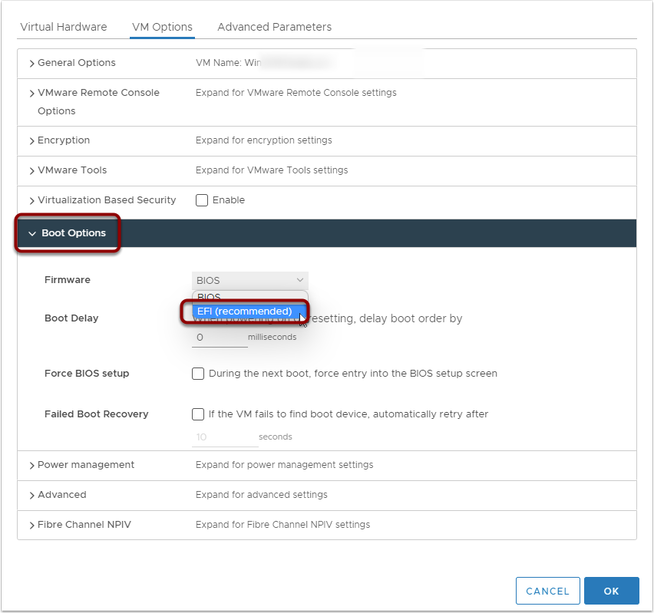

 RSS Feed
RSS Feed